How blockchain works
Overview
As described on the previous What is blockchain page, from a high-level perspective a blockchain is a 'digital ledger' which has many functionalities and use cases. It can also be thought of as a digital methodology to store data, whereby the data is encapsulated in blocks, and once the blocks are chained together they cannot be changed or altered, thus making them immutable. Once a block of data is added to the blockchain it will remain publicly viewable to anyone at any time, assuming it is a public blockchain. This is a highly beneficial system as in general as long as the blockchain is still active, and the history is still retrievable, then this results in ensuring that all the records can be verified. For example, these could be virtually anything such as medical records, financial transactions, property rights, etc.
To start to break down how the blockchain works, and before we delve into the detailed contents of a block, firstly we need to understand how the blocks are linked together, this is accomplished by using Cryptography. Therefore, each block contains a cryptographic hash of the previous block and its included transaction data. This will be explained in more detail further in this section. As previously mentioned once finalized, the blocks are immutable and cannot be changed retroactively. The only way this could be achieved would be by altering the subsequential blocks, which would require the consensus of the entire network.
Key characteristics of blockchain
There are 4 core characteristics attributed to the blockchain which are covered below:
-
Decentralization – This can be defined as storing the blocks over a network of nodes, and not in any one central location. The contents of each block in a public blockchain can be accessed by any node on the network, as they are essentially network copies that are present on all participating nodes. Therefore, there is no central entity that holds any control to change each block in the chain, so this results in decentralization.
-
Consensus Driven – A consensus model independently verifies each block on the blockchain, and provides certain rules for validating a block. For example, concerning Bitcoin, this is known as the mining process. Different types of consensus models will be covered further in this section, however, suffice to say that a consensus model can function independently, and does not require any form of central authority.
-
Immutability – A blockchain can be considered an unchangeable and irreversible record of transactions. Hence, once a block is finalized, which is the point whereby the parties involved in such a transaction are in agreement, and therefore the transaction cannot be reversed or altered in any way, it is then added to the blockchain.
-
Transparency – A public blockchain by its very nature provides total open transparency. A full transaction history can be viewed by any party, as it is in effect an open file. Therefore, another highly beneficial advantage is that a blockchain creates provenance, as all transactions can be easily audited from the first to the last entry.
Public, private, and permissioned blockchains
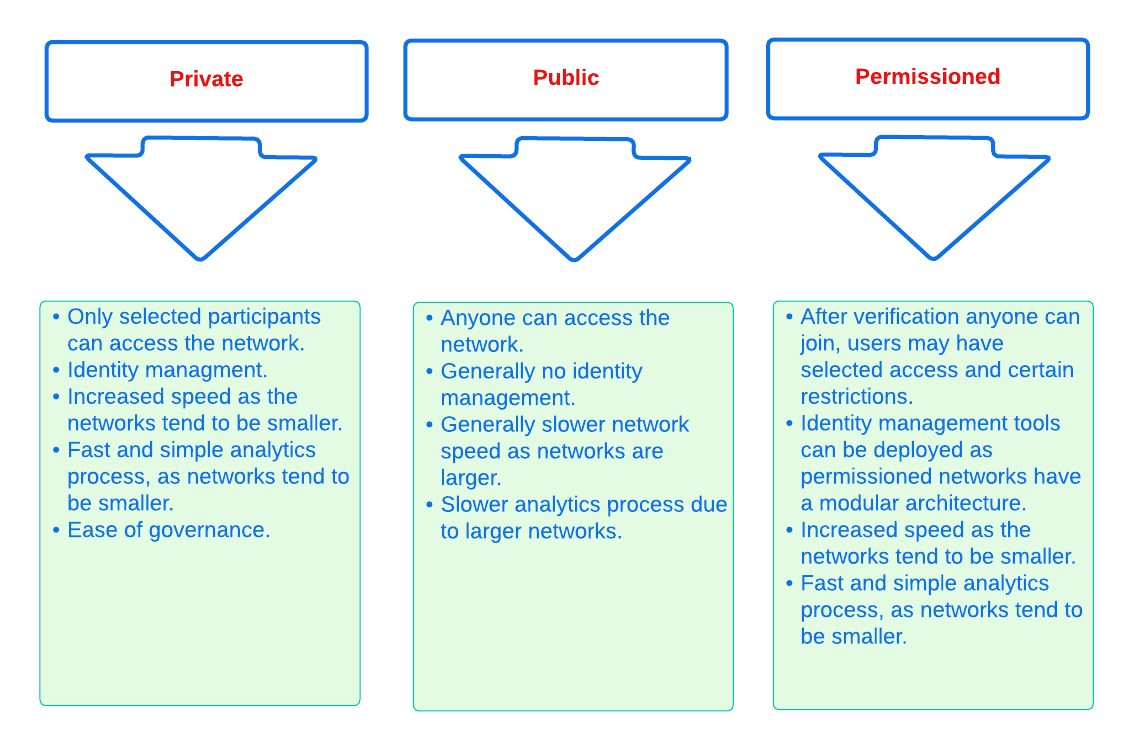
Broadly speaking there are three common varieties of blockchain currently existing which consist of public, private, and permissioned blockchains. A public blockchain is the most common type and consists of a decentralized peer-to-peer based network. Whereby a private blockchain is usually managed by a network administrator, thus being controlled by one or more entities. Only selected verified participants may access a private chain.
A definition for the main difference between the two is that private chains are only partially decentralized, as public access is not allowed. Therefore, the difference comes down to the level of access that is given to the users. In addition, permissioned blockchains are a mixture of private and public blockchains and may be customized to suit the requirements.
Examples of private blockchains are usually internal blockchains run by private businesses. In addition, business-to-business virtual currency exchanges such as Hyperledger or Ripple are also private chains. On the other hand, public blockchains are the likes of Ethereum and Bitcoin whereby anyone can access the chain and add and transact blocks. Finally, regarding permissioned blockchains, certain banks operate permissioned blockchains, which are run via a designated number of internal nodes that can be used to track money transactions. Other examples are the likes of Quorum and Corda, as generally, they offer a more cost-effective solution coupled with a better governance structure.
In summary, although public and private blockchains have gained more traction and have become more widely known, the permissioned blockchain is now seeing increasing usage, as one of the key attributes is that it allows limited activities to be controlled, even by external entities. An overview comparison of the private, public, and permissioned blockchain networks can be seen in the table below.
An overview of various blockchain networks
Consensus mechanisms
It is important to understand consensus within the blockchain ecosystem. A consensus mechanism is a methodology deployed by nodes to agree on, and validate the data content of a block before it becomes part of a blockchain. The consensus algorithm is responsible for ensuring that the same copy of the data encapsulated in each block exists within each node. To put it in a nutshell, a consensus mechanism can be thought of as a necessary procedure that results in ensuring all peers of a blockchain network come to a common agreement on the current state of the network.
Various consensus mechanisms exist today, however, the 4 main mechanisms that are widely used consist of the Proof-of-Work, Proof-of-Stake, Delegated-Proof-of-Stake, and Byzantine-Fault-Tolerance mechanisms, which are explained below:
Proof-of-Work
Proof of Work is probably the most well-known and established consensus mechanism, as it is utilized by Bitcoin. Creating a block in PoW requires the nodes to solve an arbitrary mathematical problem or complex equations, which prevents the network from being hacked, and also provides a high level of security. The term 'Proof of Work' stems from how the crypto miners effectively 'prove' that they have accomplished the necessary tasks to create a correctly formed block of transactions that will be added to the blockchain. As shown in the image above, this can be thought of as a competition whereby the miners are attempting to outdo each other by using a significant amount of energy to mine a block. In reality, this is achieved by solving complex mathematical equations which are only solvable by a try-and-error approach, which in turn then allows them to add the next block to the blockchain. Hence, this results in the miners receiving a reward for this in the form of tokens or coins. For more information, see Proof of Work (PoW).
Advantages of PoW
-
Fair Competition: The miners are incentivized to acquire blocks by improving their efficiency and speed.
-
Security: Generally, PoW from a data authenticity and security perspective is considered to be superior. The data encapsulated in the blocks in a PoW network is a history of human choices, therefore this negates the possibility of cheating in such a system that verifies every single transaction. Furthermore, with PoW a high capital investment in hardware is required, coupled with the expenditure of resources required to run this hardware which enhances the security of this type of network, as opposed to a PoS network that only requires a single low-cost outlay for any user to participate in.
-
Unused energy: In remote locations where energy is going to waste, it can be turned into a source of value by deploying the necessary hardware, together with an internet connection to begin mining.
-
Potential transition to renewable energy: As miners are mindful and well aware of their energy costs, the transition to deploying renewable energy sources are becoming more and more prevalent.
Disadvantages of PoW
-
Energy consumption: When compared to the other consensus mechanisms, it is somewhat inefficient as it requires a high amount of energy and processing power which is often attributable to the degree of competition between the miners to mine a block & win the block reward, therefore this results in being rather cumbersome, energy-intensive, and expensive to operate.
-
Vulnerable to attacks: PoW can be vulnerable to malicious attacks (e.g. the well-known 51% attack). A 51% attack can occur when either a malicious actor or a group of malicious miners acquire control of more than 50% of the network’s mining hash rate. Generally speaking the lower the hashrate (computing power), the higher the chance of a 51% attack exists. However, all consensus mechanisms are vulnerable to these attacks. This type of attack can corrupt the network as with such a high amount of mining power, they can mine faster than all other miners. In addition, they can also halt the confirmation and order of new transactions resulting in the network being interrupted. For more information, see The 51% Attack on Blockchains: A Mining Behavior Study. Additional attacks that may occur are Sybil attacks and DDoS (Distributed denial of Service) attacks. A Sybil attack is whereby the attacker can fill the network with users that he or she can control, and perform nefarious actions. In essence, this consists of having multiple network nodes that can act in unison to control the PoW mechanism. A DDoS attack is not specific to the blockchain, although it involves the attacker sending vast amounts of data to a node, therefore, rendering it unable to process these transactions, at which point the attacker would then be able to send new nodes under his control to the network resulting in a Sybil attack as described above.
-
Electronic waste: Due to the perpetual innovation and advancement in chip technology, this results in rendering the older chipsets obsolete, as the miners continue to upgrade to compete with each other with regard to the speed and efficiency of their hardware.
-
Energy traceability: As PoW mining rigs consume high quantities of energy, the authorities are easily able to trace such high energy usage, and shut them down.
Proof-of-Stake
To explain PoS briefly, users can stake an asset/token which in turn opens up the possibility to be chosen as a validator of a new block.
| Staking is defined as a number of tokens/assets that are actively held or locked by an account for a certain period. This enables these assets to be used to achieve consensus and results in the user receiving a reward. |
The proof-of-stake mechanism uses an algorithm designed to select users that have the highest stakes as validators. The highest stakeholders are expected to have a high motivation to keep the network secure and healthy, as users with the highest amount of tokens or coins have the most to lose if something goes wrong in the network. Subsequently, it is in their interest to ensure the network continues to grow. Therefore, the PoS algorithm favors users with high amounts of tokens and provides them with a much higher chance of being selected as the next validator, as compared to users with a smaller stake of tokens. This is highly beneficial for consensus building and eliminates the need for complex mathematical calculations, hence reducing the overall computing power and energy required.
Advantages of PoS
-
Efficiency: Proof-of-Stake is far more efficient than PoW as it does not require any energy-intensive computer hardware to secure a transaction.
-
Throughput increase: PoS does not require such complex cryptographic mathematical problems to be solved to complete the mining process. In addition, as PoS is more energy efficient than PoW, this results in new blocks being added to the chain with minimal effort and energy required.
-
Ease of participation: With PoS there is a much lower barrier of entry, as to achieve earning rewards there are no high costs for specialized hardware required.
-
Decentralization: As with PoS it is affordable and easy to run a node, this increases the number of users, which in turn increases the decentralization.
-
Adaptability: The PoS mechanism is more versatile than PoW and fits more blockchain use cases.
Disadvantages of PoS
-
Token consolidation: One of the well-known disadvantages relates to the fact that the mining power in PoS is determined by the number of tokens that a validator has staked, therefore it is often said that this tends to benefit the wealthy participants. Hence, users that stake more tokens have a higher chance of being chosen to generate new blocks.
-
Complexity: The block validation selection is regarded as somewhat complex, and has to be protected against DDoS attacks.
-
Centralization: Assuming a block validator holds a high percentage of staked tokens, which can be easily affordable, this could lead to the situation whereby a user could maintain and hold an unhealthy high influence in the staking pool, resulting in preventing the distribution of other newly created tokens amongst other users.
Delegated-Proof-of-Stake

DPoS works similarly to PoS, however, one of the key differences is that it utilizes a delegation and voting mechanism, where users deploy their staked collateral to vote for delegates. Every user account can register as a delegate by spending a certain amount of tokens. A predefined number of delegates with the most votes are allowed to add new blocks to the blockchain in turns. A delegate who has enough votes to be allowed to forge is called an active delegate. The forging process is divided into forging rounds. A forging round lasts until all the blocks in that round are forged. After each round, the list of active delegates is calculated again based on their current number of votes. To allow this mechanism to be both efficient and effective at performing transaction validations, various components of DPoS exist. In this system, generally users, or as they are known in DPoS, delegates are voted in based on their reputation.
DPoS utilizes a unique election system that can select users that can perform block verification. In this system, generally, delegates are voted in based on their reputation or (financial) incentives that they offer to their voters. Delegates can also be thought of as witnesses or users producing blocks. With DPoS, it is possible to vote on delegates by entering your tokens into a staking pool and linking them to a specific delegate. In DPoS a limited number of delegates exist (usually from around 20 to 100), and the delegates are voted in by other users. So the users that are chosen to generate each block, may not be the same users who were chosen to generate the preceding block. In addition, it is this limited number of delegates that oversee the governance of a blockchain deploying the DPoS consensus mechanism. Each user who holds a minimum of one token/coin with the DPoS blockchain can vote specifically for the delegates that they want to perform the transaction validations. Dependent on these votes, certain delegates are allowed to add blocks to the blockchain in a specific order.
Advantages of DPoS
-
Scalability and speed: The DPoS mechanism provides faster transaction processing times than PoW. This in turn is beneficial for many applications that require a high level of scalability. This is realized in DPoS, as there are only a limited number of delegates, which enables a consensus to be reached much faster than in PoW.
-
Energy efficiency: DPoS is more energy efficient and requires less computing power and cumbersome hardware as compared to PoW.
-
An incentive to behave and conform to the rules and security mechanism: Should any malicious activity on the network be discovered, the participants can vote to have the offending delegate removed immediately, therefore providing a good incentive for delegates to behave correctly, hence enhancing the security.
-
Fewer hardware requirements: Users do not require specialized complex hardware equipment, a regular computer is adequate to create a node and start.
-
Democratic system: With DPoS all delegates are elected democratically resulting in each delegate being able to have their say.
-
Improved distribution of rewards; All the users that maintain tokens in their accounts can select a group of delegates to perform this task. Furthermore, with this stake-weighted voting mechanism as previously mentioned, DPoS has the advantage of being able to execute transactions and verifications much faster than PoW.
Disadvantages of DPoS
-
Partially centralized: DPoS can be considered as a partially centralized system, therefore the delegates with more tokens tend to have more power in the network, as a limited number of users can retain control of the network. One criticism that is often levied at DPoS is that it sacrifices decentralization for scalability.
-
Susceptible to attacks; DPoS can be vulnerable to attacks as often there are only minimal participants in charge of keeping the network functional, therefore it could be relatively easier to organize a 51% attack.
-
Delegates could create cartels: With DPoS this could be achieved by certain delegates concentrating the role of forging between a small number of users, resulting in less resiliency and decentralization.
|
The PoS used by Klayr is more of a middle ground between PoS and DPoS. The DPoS-related characteristic is the ability of users to register as validators and then receive stakes from other users, to increase their validator weight. The PoS-related characteristic is the requirement for validators to self-stake a certain amount of tokens, to increase their validator weight. Another PoS characteristic is the mechanism for the selection of the two random standby validators, who are selected every block generation round. The higher the validator’s weight, the higher the chance to be selected in one of the two random spots available for standby validators. |
Byzantine-Fault-Tolerance
The BFT mechanism was designed in a manner whereby it can tolerate failures in the network, coupled with being able to withstand malicious attacks and corrupted data. In a nutshell, the BFT mechanism ensures that the same consistent data is received by every node present in the network at any time, whilst also allowing consensus to be reached regardless of some of the node’s failures.
Firstly, there are 3 key features whereby BFT improves the blockchain, and they are listed below:
-
Safety: If 2 conflicting blocks occur on the network, then assuming two-thirds of the active validators adhere honestly to the protocol, these 2 conflicting blocks will not be finalized simultaneously on the blockchain.
-
Accountability: In the case whereby the protocol is violated by the validator, they will be held responsible for this. The key requirements for BFT must be accomplished by the nodes within a blockchain network, therefore, it is imperative they are deterministic and must begin with the same state for practical BFT.
-
Liveness: New blocks can still be finalized on the network, even in the case whereby one-third of the active validators are offline.
To achieve BFT consensus the following requirements must be met:
-
Termination: Every known faulty process must conclude with a result or output.
-
Agreement: The same output is decided by every non-faulty process.
-
Validity: Every process starts with the same input.
-
Integrity: The consensus value and all non-faulty process decisions achieved in point 2 above, need to have been put forward by some non-faulty process.
Advantages of BFT
-
Robustness: the BFT consensus approach allows the network to remain intact if one of the nodes fails.
-
Fast transactions: The agreement and transaction timing are guaranteed in a BFT network, as they are not affected by any faulty or malicious nodes.
-
Energy efficient - As transactions do not require numerous verifications, once all the network nodes reach consensus over a cluster of transactions the block is immediately verified, hence there is no need for a high amount of computing power.
Disadvantages of BFT
-
Vulnerability to attacks: If the majority of the users work together maliciously, the network can be vulnerable to the 51% attack scenario.
-
Reduction in scalability: To ensure the network functions correctly, the distribution of the network needs to increase and expand, however, more nodes in the system result in a reduction in scalability.
Cryptography
Cryptography is not a new concept and ultimately is used to ensure secure communication between 2 parties can be established over an unsecured connection.
-
How is this used in blockchain?
Cryptography in blockchain consists of 3 different types, symmetric, asymmetric, and cryptographic hashing, and are explained further in this section. These play an important role in blockchain in maintaining security and are the underlying technology for securing wallets and performing transactions. For example, When creating a wallet on a blockchain, a public-secret key pair will be generated.
-
Why is it used and what are the advantages?
Cryptography is used simply to secure the various transactions occurring on the blockchain network and to verify the transactions such as minting or transferring tokens or coins. It is mainly deployed in the application and consensus layers of the blockchain. Furthermore, being able to store and protect large amounts of transactions, and provide protection from hackers or malicious actors is considered highly advantageous.
To delve a bit further into cryptography in blockchain, more detailed information can be found in this article on Blockchain Cryptography: Everything You Need To Know. However, it is helpful to be aware of the 3 types of cryptography deployed today. These can be broken down into the following three types described below:
Symmetric Key Encryption
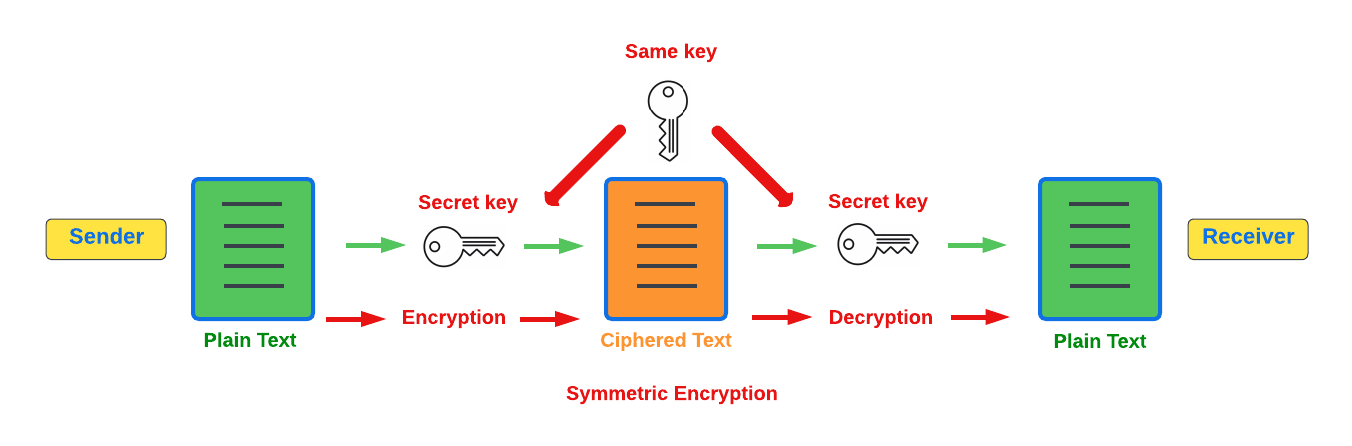
This is the simplest method, as 1 common key is used for both the encryption and decryption process, and is also referred to as secret-key cryptography as shown in the illustration below. In this case, it is necessary to ensure the transfer of the common key can be performed safely from the sender to the recipient. Symmetric cryptography is used in the banking sector, a good example being card transaction payment applications. Examples of some of the most widely used symmetric encryption algorithms are AES, Blowfish, and RC6. However, although it offers secure protection, it is necessary that all parties involved have to exchange the secret key that has been used to perform the encryption before it can be decrypted. Nevertheless, blockchain uses an even more enhanced encryption methodology known as Asymmetric Encryption, as described in the following paragraph.
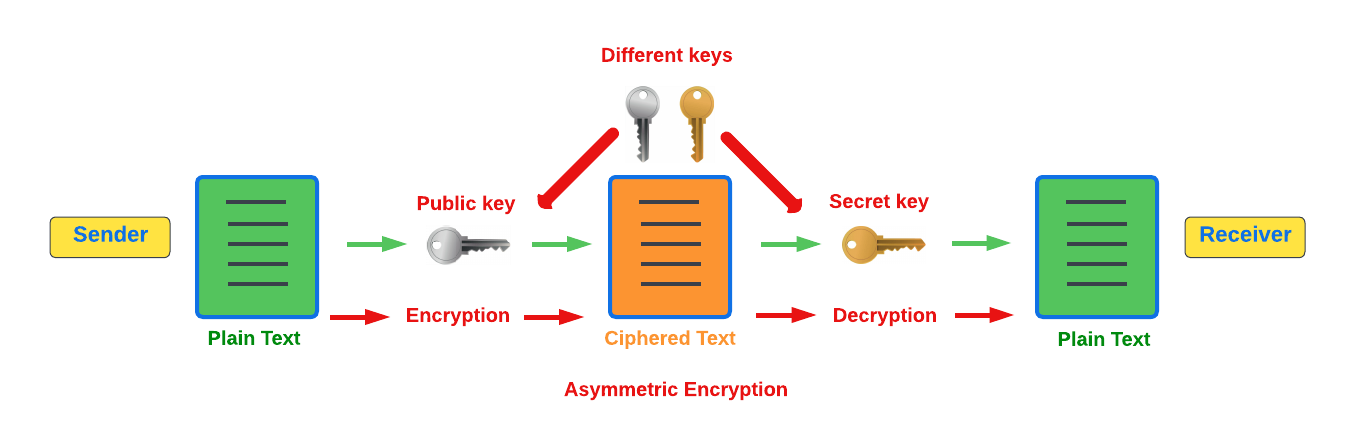
Asymmetric Key Encryption
This type of encryption functions by using a pair of keys. This comprises an encryption key, and a decryption key, and is more commonly known as a public key and a private (or secret), key. The algorithm deployed for this method generates both a secret, key and a unique public key. The secret key as its name implies, is kept secret, and the public key is openly shared. Furthermore, the asymmetric encryption method has an additional element of security, although the symmetric method of encryption is faster, nevertheless, they are both very effective.
It is quite common with regard to the management of cryptocurrencies that with the asymmetric model of encryption, the public key is generally the actual address that 'contains' the tokens or coins, and is publicly viewable. Therefore, when a transaction is created, this has to be digitally signed with the secret key. Once this has been received by the blockchain network, it can be verified with the same public key, therefore this proves the authorization of the transaction is genuine by the owner of the secret key or any entity with knowledge of the secret key. In asymmetric encryption, anyone can decrypt the message using the owner’s public key so this does not keep the identity of the user confidential. Nevertheless, the sender’s identity can be verified, as if the associated public key decrypts the data, then it is only possible that it could have been encrypted with the user’s private key. Subsequently, the public key is used for identity management and the account address, and the secret key is derived from the passphrase of the user account to access the funds in the account associated with the address, and hence is able to authorize and then perform any actions required. The recipient can only decrypt the ciphered text if he or she holds the identical symmetrical encryption key. Therefore, this can be transmitted over an unsecured medium, as regardless of any third party or malicious actors intercepting this, they would not be able to decrypt the text, rendering it useless to them.
Hash Functions
This function does not utilize any keys, as it takes the contents of the plain text and deploys a cipher, which is used to generate a hash value of a fixed length from the plain text. Hence, the contents of this plain text can’t be unraveled from the cipher text. Therefore, hashing outputs can be used to efficiently verify the inputs without revealing the input itself. In the context of blockchain, the hashing function properties are used mainly within the consensus and application domains. A popular use case for hashing in the blockchain is to create a hash of the previous block and include that hash in the next block. This way, a block is cryptographically connected to all its former blocks, forming the classical chain of blocks. Even the smallest change in one of the former blocks would create a very different hash of that particular block, which wouldn’t match the hash in the header of the next block. This would break the chain of blocks immediately. Therefore, hashing is an important factor to ensure the immutability of the blockchain.
A hash converts the required data into a string of characters. Hashing is able to store data efficiently, as the hash is of a fixed size, and in addition, provides security through encryption. Other hashing functions are also used in the blockchain world, for example, Ethereum deploys the Keccak-256 cryptographic hash function. There are numerous benefits of hashing, as it meets the encrypted requirements demanded by a blockchain network. Its characteristics consist of being able to accept a message of any length, whilst producing a fixed-length message digest. Furthermore, the hash is irreversible, ensuring it is impossible to generate any message from the message digest.
As described earlier on the What is blockchain page, it is also deterministic and is the key component in providing immutability of the blockchain data as well, which as we have learned is highly beneficial.
Klayr maintains a cryptography package that contains all the cryptographic functionalities required when interacting with the Klayr ecosystem and can be used on both the server and client sides.
State machine
A State machine is considered to be a concept whereby the definition relates to a machine that can have multiple states, however only one state is possible at any one given time. Hence, a state, in this case, refers to the current state of the blockchain system and the transactions are a way to transition from one state to another with regard to a blockchain system, it can be deemed as a deterministic, replicated state machine.
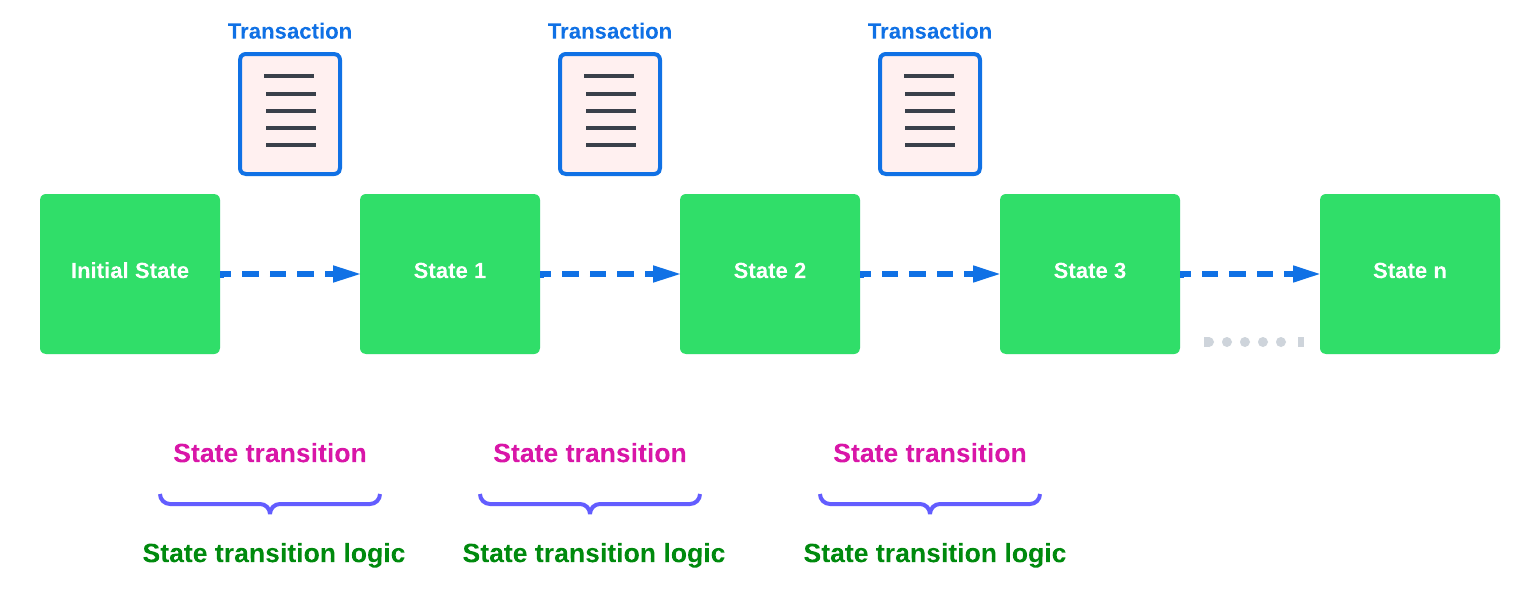
The state transition refers to the changes that occur in the state machine after a specific event has occurred. Therefore, it is best thought of as a reference to the process of moving from 1 state to another via transactions. Although it should be noted that even a block that does not contain any transactions also can alter the state of the blockchain. Furthermore, it maintains a temporary state that exists during the processing of a block.
Now that we have covered how blockchain functions, the next step is to look at the extensive range of user-friendly Klayr products that will enable us to create and manage our blockchain applications.